If you’ve used the community version of the Kong API gateway, you have probably noticed that anyone that knows the server name or IP for your Kong community API gateway can access and modify existing objects including services and routes. To set up and use role-based access control Kong Enterprise version provides additional capabilities.
In this example, we will leverage the Kong Enterprise on RHEL 7 lab instance we set up earlier. You can read the install steps here.
Before getting started, please make sure enforce_rbac=on is in the kong.conf file.
Log in to https://<Kong-Enterprise-VM-IP>:8445/login using kong_admin as the username and the password you set during the install process (this is the same password you assigned during the step of EXPORT_PASSWORD=’password’)
Click on Teams -> RBAC Users
Create a new user rbac_user_1 with a token of rbac_user_token_1
Make sure that enabled checkbox is checked
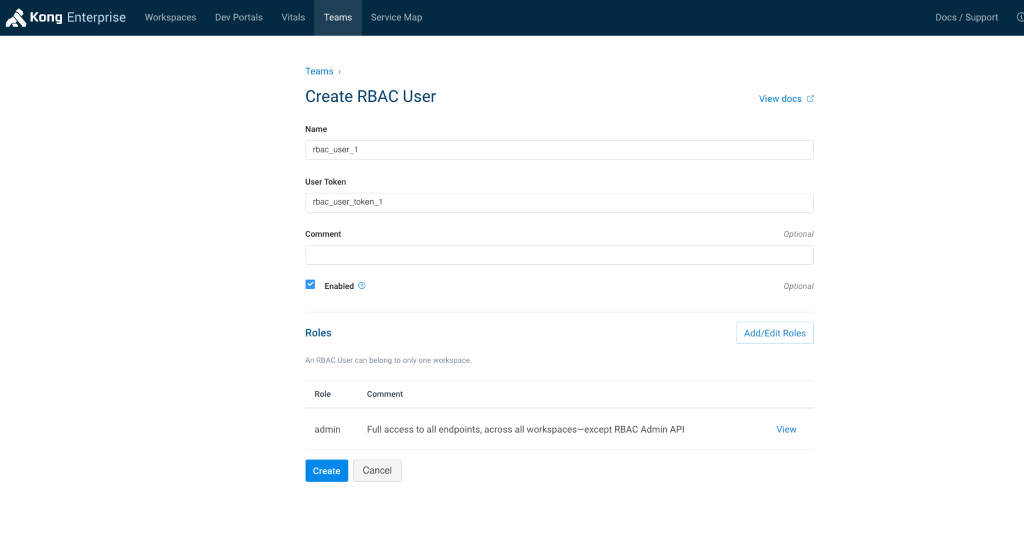
Add roles –> admin
Note that we are creating this user with ‘admin’ permissions, but not ‘super-admin’. So it will have access to all endpoints, across all workspaces—except RBAC Admin API.
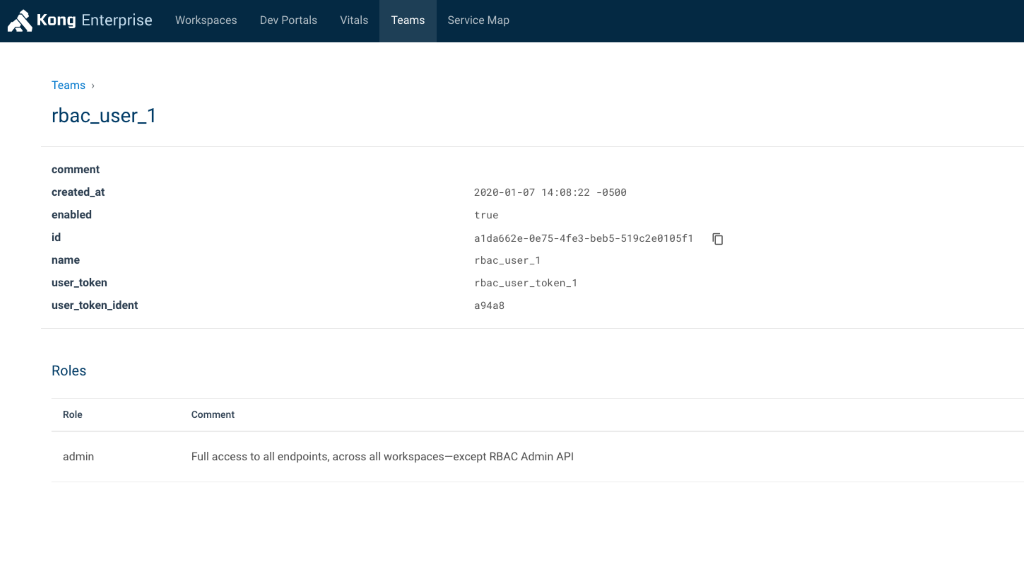
A new RBAC user, rbac_user_1, gets created
Now let’s try and test the RBAC setup. We will use Postman (https://www.getpostman.com/) for this example.
First we will create a new Collection labeled ‘Kong Enterprise‘ and then a new Request within that Collection called ‘Get Services’.
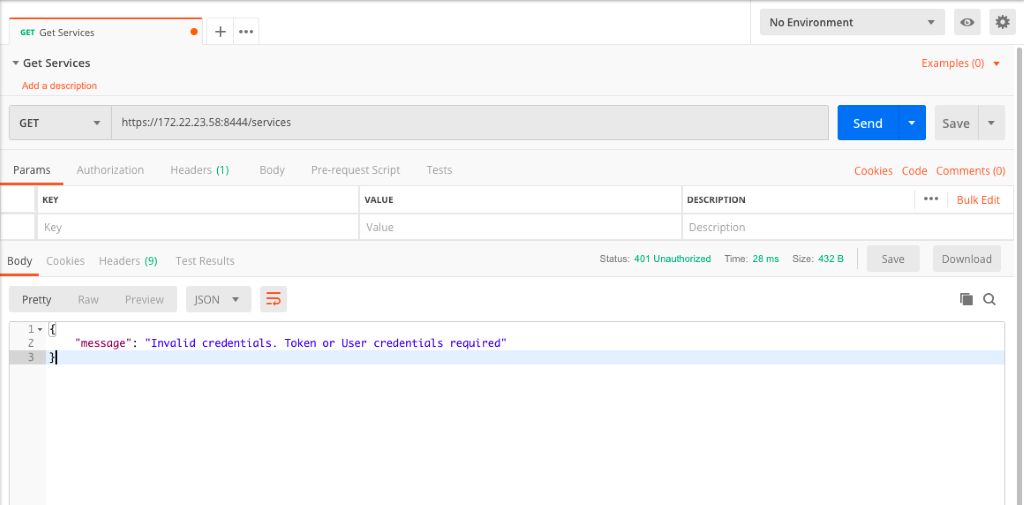
Next, we will try to run a GET request against https://<Kong-Enterprise-VM-IP>:8445/services to list out all available services. If you don’t pass any headers or credentials, you get the error notification “Invalid credentials. Token or User credentials required”.
By adding the header with Kong-Admin-Token and the value of the token set in the earlier step ‘rbac_user_token_1‘, we try to run the request again and this time it succeeds
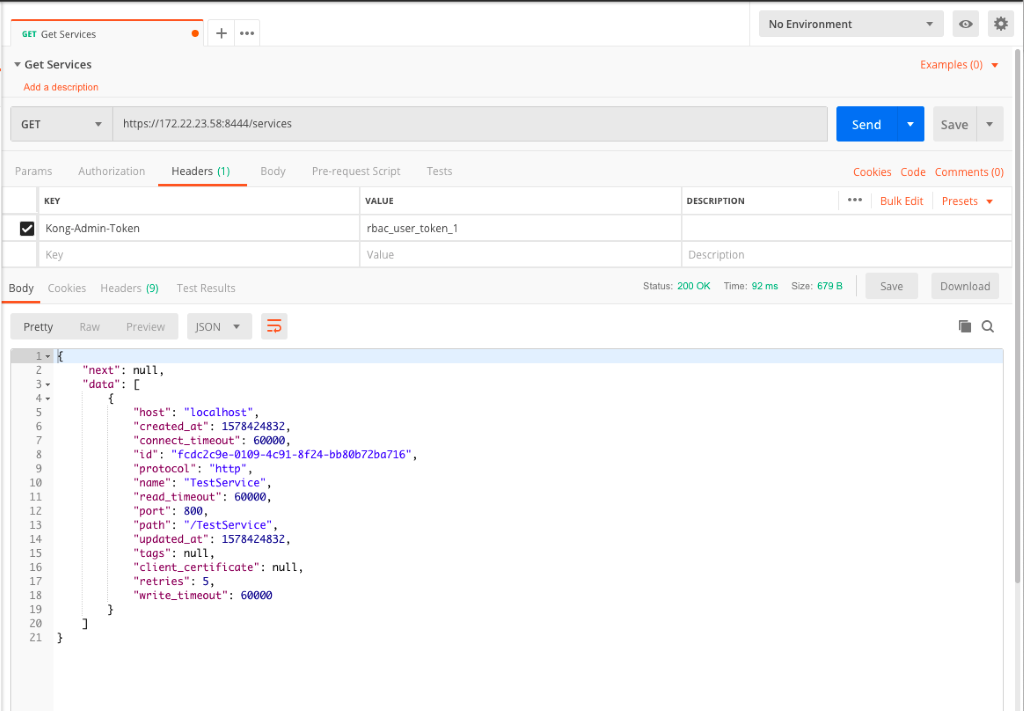
As you can see, with RBAC enabled, Kong Enterprise provides much greater control over who can access and modify various objects. The user permissions can be tailored to suit various team needs – depending upon how granular you want access to be.
If you have any questions or comments on the tutorial content above, or run in to specific errors not covered here, please feel free to reach out to info@keyvatech.com

Chief Technology Officer
Anuj Tuli is the chief technology officer at Keyva. In this role, he specializes in developing and delivering vendor-agnostic solutions that avoid the “rip-and-replace” of existing IT investments. Tuli helps customers chart a prescriptive strategy for Application Containerization, CI/CD Pipeline Implementations, API abstraction, Application Modernization, and Cloud Automation integrations. He leads the development and management of Cloud Automation IP and related professional services. With an application developer background, he provides a hands-on perspective towards various technologies.
Like what you read? Follow Anuj on LinkedIn.
Join the Keyva Community! Follow Keyva on LinkedIn at:
